CSS Computer Science Past Paper 2021
PAPER-I (Subjective) 80 Marks
Attempt ONLY FOUR questions from PART-II. (20×4)
PART-II
SECTION-A
Q. No. 2
(a) What are office productivity tools? Explain the uses of any two productivity tools in your home or workplace.
(b) Write a detailed note on computer crimes and ethical challenges.
(c) What are the different types of computers? Explain the benefits of miniaturization.
Q. No. 3
(a) Describe any two of the following briefly: ISP, HTML, SSD, Cloud Computing.
(b) Write a program that should output the factors of the number passed as input – one factor on each line. Factors of a number, say x, are those whole numbers which can be multiplied with other whole numbers to get x.
(c) What are IDEs? How do they help in software development? List the IDEs you have ever used.
(d) Write a program in C/C++ to convert a decimal number to hexadecimal.
Q. No. 4
(a) Explain the object-oriented programming paradigm. Write a detailed note on any two of the principles of the object-oriented programming paradigm.
(b) Why do we need interfaces in OOP? How does it help in achieving abstraction?
(c) What do you mean by runtime and compile-time errors?
SECTION-B
Q. No. 5
(a) What is a tree in data structure? Describe its types with the help of examples.
(b) What is pass by value and pass by reference? Can we pass an object as a parameter to call a method in Java?
(c) Convert the following infix notation to prefix:
(i) (30+23)(43-21)/(84+7)
(ii) 2(1+(4*(2+1)+3))
Q. No. 6
(a) Convert the following NFA to DFA:
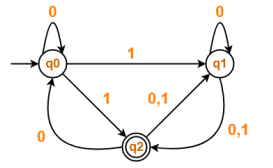
(b) Differentiate between overloading and overriding with the help of an example.
(c) What is recursion in data structures? Explain three conditions of a recursive function with the help of an example.
Q. No. 7
(a) Write detailed notes on any TWO of the following:
- PERT chart
- Unified Modeling Language
- AVL Trees
(b) What is a Software Process Model? Explain the Spiral model in detail.
(c) What do you mean by software quality? List at least five quality attributes.
Q. No. 8
(a) Consider the grammar:
S → cAd
A → a b | a
Construct a top-down parse tree for the input string w = cad.
(b) Is the above-given grammar ambiguous or unambiguous? Justify your answer.
(c) Write similarities and differences between CFG and regular expressions.
(d) Design grammar for the following language:
“The set of all strings of 0s and 1s such that every 0 is immediately followed by at least one 1.”
(e) Write a note on Aspect-Oriented Programming.
PAPER–II (Subjective) 80 Marks
Attempt ONLY FOUR questions from PART-II. (20×4)
PART-II
SECTION-A
Q. 2
(a) The addressing in a typical instruction format is done by using different addressing modes. Examine any five addressing modes with an example based on the contents of the address field, actual address, and contents of the memory location.
(b) The decimal value of the address field in an instruction is 120. The addressing mode of the machine’s architecture is register direct and register indirect addressing. Calculate the address of the corresponding operand.
(c) Compare the set of addressing modes of RISC and CISC machines. Give one example of addressing modes used in RISC and CISC respectively.
Q. 3 Memory managed by BITMAP is shown below:

(a) Show properly filled memory according to the BITMAP where memory index starts from zero.
(b) Insert a page H of size 3 allocation units in memory drawn in part ‘a’ using the first-fit algorithm. Redraw memory and the BITMAP after insertion.
(c) Now insert another page K of size 2 allocation units in memory drawn in part ‘b’ using the next-fit algorithm. Redraw memory and the BITMAP after insertion.
(d) Use a linked list data structure for the above memory mapping (only give the equivalent figure).
(e) Use a hash table to keep track of active pages in the above memory (only give the figure).
Q. 4
(a) Calculate effective memory access time using the following data:
- TLB hit ratio is 85%
- TLB access time = 20 nsec
- Memory access time = 115 nsec
Effective memory access time = Hit rate * (TLB access time + Mem access time) + (1 – Hit rate) (TLB access time + Process_table access time + Mem access time)
(b) Consider a logical address and physical address of 31 and 22 bits, respectively. What will be the total logical and physical address space?
(c) Does the resource allocation graph shown below consist of a deadlock or not? Justify with reason.

(d) What is a race condition? What are the different techniques to avoid race conditions in the processes? Which one is optimal and why?
Q. 5
(a) Compare Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). How are they used in wireless networks?
(b) What mechanism is used by TCP to protect itself from misdelivery?
(c) Calculate the TCP window size to fully utilize the line on which the WAN link is 2 Mbps, and the RTT between source and destination is 300 msec.
SECTION-B
Q.6
Consider the following database schema and write the relational algebra expression for the following queries.
Students (Stu_Reg, Stu_Name, Stu_Address)
Instructor (Ins_ID, Ins_Name, Ins_Dept_ID)
Course (Cr_Code, Cr_Title, Cr_CrHours)
Dept (Dept_ID, Dept_Name)
Results (Res_Stu_Reg, Res_Cr_Code, Res_Marks, Res_Ins_ID, Res_Grade)
(a) Write relational algebraic expression for:
(i) To display all the students details in section BSSE.
(ii) To display all Instructor Names and their respective Department Names, (if an instructor is not assigned any Dept his name should be displayed as well).
(iii) To display Stu_Reg, Stu_Name, Cr_Code, Cr_Title and Res_Marks for students who got 75 or more marks.
(iv) To display Res_Stu_Reg, Ins_Name, Res_Grade for Instructors whose Dept_ID is 1.
(b) What is the concept of a gerund in databases? Provide an example of a gerund. Is it essential to eliminate gerunds from the database? If yes, explain how; if no, explain why.
Q.7
(a) Write code or pseudocode to locate all of the large boxes in the image using morphological image processing.

(b) Is there a need for more than one color model? Mention different color models and their uses.
(c) Explain the CMY color model, its uses, and how it differs from CMYK.
Q.8
(a) Analyze the following code and draw the resulting table:
<table border=”1″ cellspacing=”0″>
<tr><td>1</td><td colspan=”3″>2</td></tr>
<tr><td rowspan=”2″>3</td><td colspan=”2″>4</td><td>5</td></tr>
<tr><td>6</td><td>7</td><td>18</td></tr>
<tr><td colspan=”3″>9</td></tr>
<tr><td>10</td><td colspan=”3″>11</td></tr>
<tr><td>12</td><td>13</td><td>14</td></tr>
<tr><td rowspan=”2″>15</td><td colspan=”2″>16</td><td>17</td></tr>
</table>
(b) What is the role of requirement engineering in web engineering? List functional and non-functional requirements for a website.
(c) What are the different security mechanisms used for encrypting the contents of a website? Explain one in detail.
