CSS Computer Science Past Paper 2019
PAPER-I (Subjective) 80 Marks
Attempt ONLY FOUR questions from PART-II. (20×4)
PART-II
SECTION-A
Q. 2
(a) Give a detailed note on a revised BSD 3-clause license. Also name 5 softwares using this license.
(b) How do artificial intelligence may facilitate us in improving cyber security?
(c) What are the main parts and phases of a computer virus program?
Q. 3
(a) See the following C++ program to declare whether an input number is a prime number or not. Identify the logical errors in the given program (if any). Give your correct statement(s) exactly at the same line number.
1. n, i;
2. bool is Prime = false;
3. cout<< “Enter a positive integer: “;
4. cin>> n;
5. for(i = 1; i< n / 2; ++i)
6. {
7. if(n /i == 0)
8. {
9. is Prime = false;
10. break;
11. }
12. }
13. if (is Prime)
14. cout<< “This is a prime number”;
15. else
16. cout<< “This is not a prime number”;
(b) What is the difference between call by value and call by reference?
(c) What is the role of preprocessor directives? Give three examples in C++.
Q. 4
(a) How do the OOP paradigm can be associated with the real-world problems? Explain.
(b) Discuss critical reasons given by the professionals for not supporting the OOP paradigm.
Q. 5
(a) Discuss the security issues associated with cloud computing.
(b) What is bit twiddling? Give a brief description.
(c) An image is a representation of some information. Discuss how does a computer represent an image internally? Name different algorithms used to extract features from images.
SECTION-B
Q. 6
(a) Discuss the limitations of genetic algorithms.
(b) What is AVL tree? Under what condition, a binary tree becomes AVL tree?
(c) Consider the following graph. Find out the sequence of edges added to the minimum spanning tree using Kruskal’s algorithm.
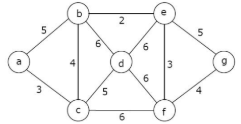
Q. 7
(a) Discuss the architecture of aspect-oriented system.
(b) Briefly discuss the motivation for aspect-oriented programming.
(c) What is the significance of quantification and obliviousness?
Q. 8
(a) Write down the major steps involved in code generation.
(b) How would you optimize a loop? Describe the techniques briefly.
(c) Differentiate machine-dependent optimization and machine-independent optimization.
PAPER–II (Subjective) 80 Marks
Attempt ONLY FOUR questions from PART-II. (20×4)
PART-II
SECTION-A
Q. No. 2
(a) Compare the main features of CISC and RISC architectures. Which type of architecture is suitable for pipelining?
(b) Demonstrate the use of the superscalar approach to achieve instruction-level parallelism using a suitable example.
(c) List all basic functions of buses in the context of computer architecture.
Q. No. 3
(a) Show field-by-field comparison for IPv4 and IPv6 packets.
(b) Explain the following routing techniques using suitable examples.
(i) Link State Routing
(ii) Distance Vector Routing
(c) Show step-by-step procedure of error detection using cyclic redundancy check method for a 7-bit code block “1001001”. Assume appropriate generator polynomial.
Q. No. 4
(a) Demonstrate step-by-step procedure for process swapping between main memory and secondary memory.
(b) Show flow chart of a process scheduling mechanism using various queues.
(c) Explain the difference between Sequential Access and Indexed Sequential Access in the context of file access using a suitable example.
Q. No. 5
(a) Demonstrate various types of multiplexing techniques in the context of computer networks using suitable examples.
(b) Show step-by-step procedure to find MAC address of a node in a network using Address Resolution Protocol.
(c) For transmission of voice signal in real time over the network, select a suitable switching technique. Justify your answer using an example.
SECTION-B
Q. No. 6
(a) Analyze the following noise models in the context of digital image processing:
(i) Gaussian Noise Model
(ii) Uniform Noise Model
(b) Compare RGB and HSI color models in the context of digital image processing.
(c) Describe the step-by-step process of the application of compression-based technique for image segmentation.
Q. No. 7
(a) A Medium advertising company is reviewing its IT requirements and is considering using a Cloud solution for web applications as opposed to investing in existing infrastructure. Is this an appropriate strategy? Justify your answer using an example.
(b) Describe briefly the role of validation in the requirement engineering process.
(c) Explain the difference between functional and non-functional requirements in the context of web engineering using a suitable example.
Q. No. 8
(a) Demonstrate the use of ER Model in the database designing process using an example.
(b) Describe an appropriate security scheme for a database maintained by a bank. Justify your answer using an example.
(c) Explain the difference between top-down and bottom-up approaches in the context of distributed database design using a suitable example.
